Malware
MaCySTe integrates as part of the attacker addon a persistent malware installed inside of the INS Network.
This malware will try to connect to his preset command and control server via WebSocket and then:
- Overhear, parse, and send in structured format every received NMEA sentence allowing the attacker to reconstruct the ship state
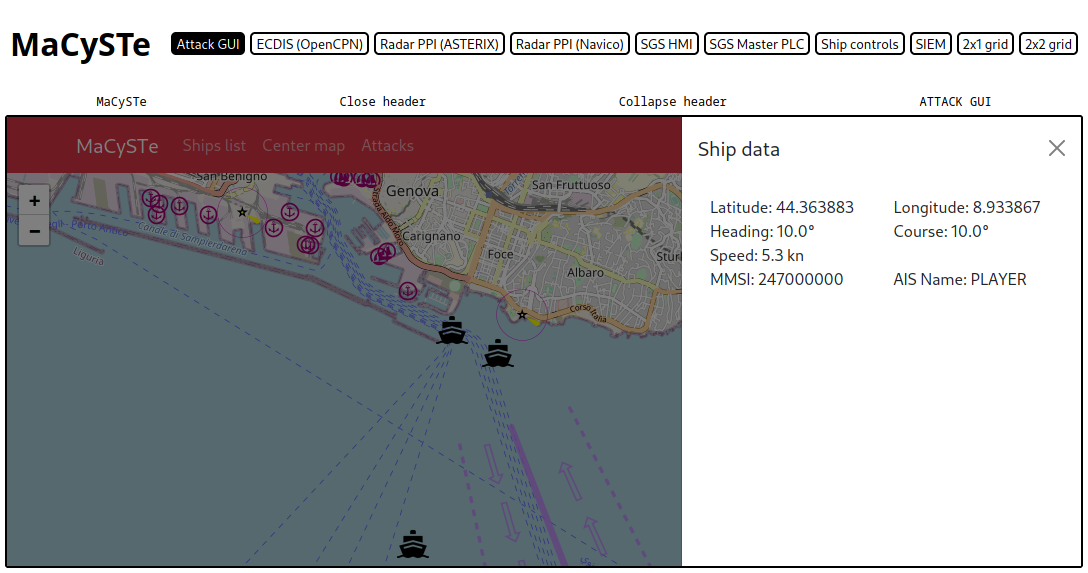
- Expose a JSON-RPC based interface for starting and stopping attacks
The malware is structured as an extensible platform, allowing users to extend it to add their own attacks with automatic GUI integration.
Attack JSON-RPC API
The malware will listen for JSON-RPC messages of the following format
{
"method": "<method-name>",
"params": [ "<param-1>", "<param-2>", "<param-n>" ],
"id": "<request-id>"
}
This example is not exactly spec compliant (it's missing the jsonrpc field)
attack_inventory method
This method allows to dynamically gather a list of available attacks
Sample request
{
"method": "attack_inventory"
}
Sample response
{
"jsonrpc": "2.0",
"result": [
{
"name": "inject_heading",
"ui_name": "Inject heading",
"description": "Injects a fictitious heading into the INS",
"parameters": [
{
"name": "heading_to_inject",
"description": "Which heading to inject",
"required": true,
"type": "number",
"min": 0,
"max": 359
},
{
"name": "injection_hz",
"description": "Frequency of the packets injection",
"required": false,
"type": "number",
"default": 1
}
]
},
{
"name": "dos_radar",
"ui_name": "DoS ASTERIX radar",
"description": "Obscure ASTERIX radar",
"parameters": [
{
"name": "range_nm",
"description": "Range to obscure in NM",
"required": false,
"type": "number",
"default": 12,
"min": 1,
"max": 24
},
{
"name": "injection_hz",
"description": "Frequency of the packets injection",
"required": false,
"type": "number",
"default": 1
}
]
}
],
"id": ":r0:"
}
attack_start method
This method allows to start an attack
Example request
{
"id": ":r1:",
"method": "attack_start",
"params": [
"dos_radar",
6
]
}
Example response
{
"jsonrpc": "2.0",
"result": {
"name": "dos_radar",
"params": [
6
],
"running": true
},
"id": ":r1:"
}
attack_state method
This method allows to check the running state of an attack
Example request
{
"method": "attack_state",
"params": [
"dos_radar"
],
"id": ":r1:"
}
Example response
{
"jsonrpc": "2.0",
"result": {
"name": "dos_radar",
"params": [],
"running": false
},
"id": ":r1:"
}
attack_stop method
This method allows to stop an attack
Sample request
{
"id": ":r1:",
"method": "attack_stop",
"params": [
"dos_radar"
]
}
Sample response
{
"jsonrpc": "2.0",
"result": {
"name": "dos_radar",
"params": [],
"running": false
},
"id": ":r1:"
}
Adding your attacks
Your attacks can be easily be implemented by extending the Attack class specifying which elements have to be set in the GUI and adding them to the available_attacks array inside of the source code.
Each attack added in such a way will be automatically rendered inside of the attack GUI with automated form validation and status reports, see the dedicated section for more details.